The price of Bitcoin has jumped by over 120% since the beginning of the year, leading many to conclude that the bear market in crypto is over. The market has not been this frothy since 2017, when we witnessed an extraordinary boom in the price of all crypto assets, as investors poured money into the market hoping to get in early with the next Bitcoin or Ether. At the same time, tech teams dreamt up new use cases for utility tokens that leverage blockchain technology and raised money to fund them via initial coin offerings (ICOs). The bubble burst in early 2018, precipitated by the revelations of fraudulent activity, regulatory action and the reemergence of rational thought by investors. Bitcoin fell by 75% and Ether and other crypto assets were down even more.
While the crypto spring may now be upon us, it does not mean we will see a return to the ICO boom. Since 2017, regulators in the U.S. and around the world have cracked down on these token launches, which they often consider to be unregulated securities offerings. This does not represent the end of tokenization, however. Many companies are now focusing on building technology and an ecosystem for security tokens. These new tokens are digital securities recorded on a blockchain and issued in full compliance with the securities regulations in the jurisdiction in which they are offered. In this way, security tokens can be thought of as the convergence of crypto, enterprise blockchain and traditional finance.
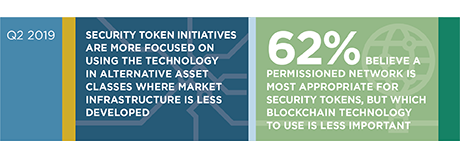
This Greenwich Associates research looks into the emerging market for security tokens, identifying the most promising applications, key advantages and leading players in the space.
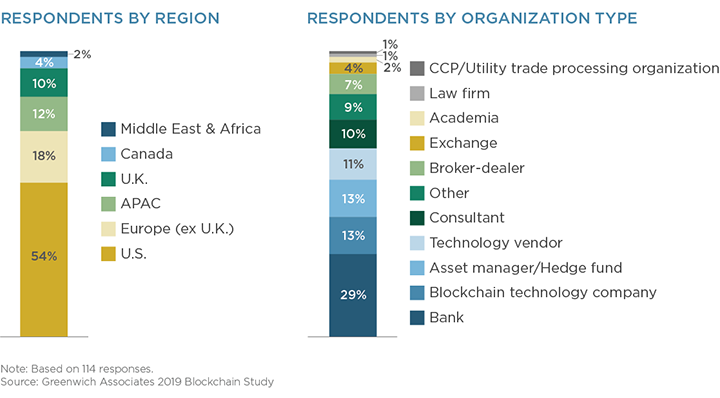
MethodologyBetween March and April 2019, Greenwich Associates interviewed 114 executives active in the blockchain and financial technology space across all of North America, Europe, Asia Pacific, and the Middle East & Africa. Seventy percent of respondents were actively involved in security token initiatives. In addition, this paper leverages data from the Greenwich Associates 2019 Equity Portfolio Manager Study, including interviews with 56 portfolio managers and analysts located in North America, Europe and Asia.